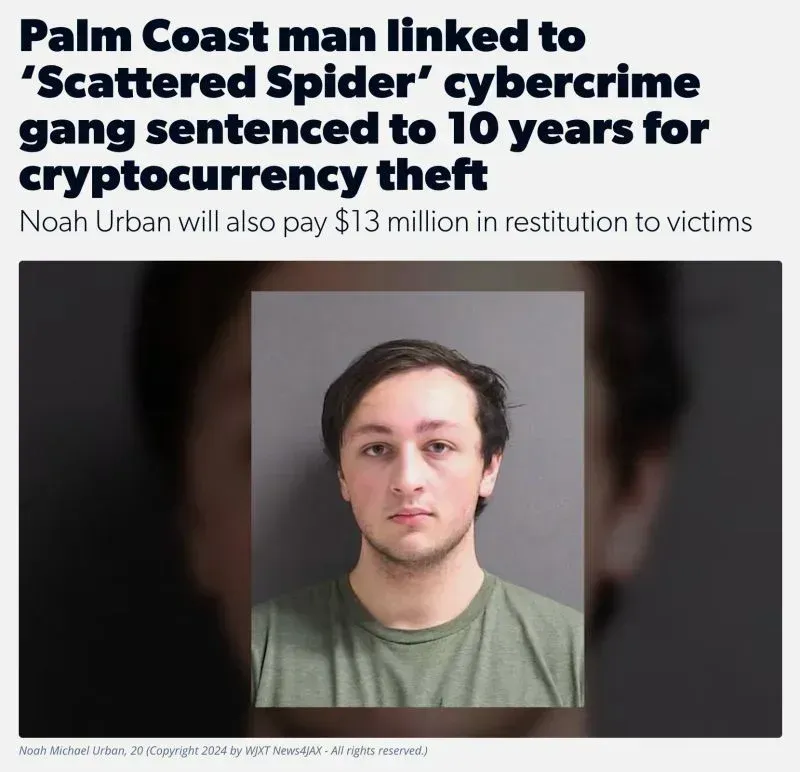
Two Teenagers Charged in £39M Transport for London Cyber Attack: Inside the Scattered Spider Threat

Major breakthrough as UK authorities arrest alleged Scattered Spider members behind devastating attack on London's transport network
In a significant law enforcement victory, UK authorities have charged two teenagers in connection with the massive cyber attack that brought Transport for London (TfL) to its knees for three months in 2024, causing £39 million in damage and disruption to one of the world's busiest transport networks.
Thalha Jubair, 19, from East London, and Owen Flowers, 18, from Walsall, West Midlands, were arrested at their home addresses on Tuesday (16 September) by the NCA and City of London Police and appeared at Westminster Magistrates Court on charges under the Computer Misuse Act.
The Attack That Paralyzed London's Digital Infrastructure
The TfL network intrusion occurred on 31 August 2024, which investigators believe was carried out by members of the online criminal collective known as Scattered Spider. While London's buses, trains, and Underground services continued running, the attack devastated TfL's digital ecosystem for months.
The breach had far-reaching consequences:
- £39 million in total damage and recovery costs
- Three months of service disruption affecting online systems
- 5,000 customers had personal banking information potentially compromised, including bank account numbers and sort codes
- 25,000 staff forced to report to offices for manual identity verification
- Critical services offline until December 2024, including photo travel card issuance and customer refunds
It was not until December 4, 2024, that TfL was able to issue photo travel cards – Zip cards for young people, and Oyster cards for the 18+ and 60+ age groups – or issue refunds to customers for incomplete pay-as-you-go journeys.
The Suspects: From Anonymity to Arrest
Owen Flowers, initially arrested as a minor in September 2024, could only be named after turning 18. Flowers was initially arrested for the TfL attack on 6 September 2024, at which point NCA officers identified further potential evidence of offending against US healthcare companies. He has since been charged with additional conspiracy counts involving attacks on SSM Health Care Corporation and Sutter Health networks in the United States.
Thalha Jubair, known online by aliases including "EarthtoStar," "Brad," "Austin," and "@autistic," faces additional charges under the Regulation of Investigatory Powers Act for allegedly refusing to provide passwords for seized devices.
The courtroom scene was striking: When Mr Flowers appeared in court, he wore a grey hoodie with "off the grid" written on it. Mr Jubair sat next to him, wearing a black hoodie and black glasses. Neither man spoke to each other during the proceedings.
International Implications: A Global Criminal Enterprise
The arrests have exposed the international scope of the Scattered Spider threat. The US Department of Justice simultaneously unsealed charges against Jubair, alleging his participation in "a sweeping cyber extortion scheme carried out by a group known as Scattered Spider" that targeted at least 120 computer networks and extorted 47 US entities, with victims paying at least $115 million in ransom payments between May 2022 and September 2025.
If convicted on all US charges, Jubair faces a maximum penalty of 95 years in prison.
Understanding Scattered Spider: The New Face of Cybercrime
Scattered Spider, also referred to as UNC3944, is a hacking group mostly made up of teens and young adults believed to live in the United States and the United Kingdom. What makes this group particularly dangerous is their mastery of social engineering rather than technical exploits.
Key Characteristics:
- Native English speakers: Primarily teenagers and young adults from the US and UK
- Social engineering experts: Specialize in manipulating human psychology rather than exploiting software vulnerabilities
- Decentralized structure: Operates more like a loose collective than a traditional crime syndicate
- Identity-focused: They exploit gaps in authentication, social engineering weaknesses, and inconsistent third-party controls to move laterally and seize entire cloud environments

Evolution of Tactics:
While Scattered Spider's early hits in 2022 and 2023 were the result of social-engineering attacks, the group transitioned to domain-based phishing through much of 2024 before activity went dormant last summer. However, they've recently returned to their roots, once again relying exclusively on social engineering as their primary attack vector.
The Broader Scattered Spider Campaign
The TfL attack is just one piece of a much larger criminal enterprise. Scattered Spider has been linked to numerous high-profile breaches:
Casino Attacks (2023):
- MGM Resorts: Week-long outage causing an estimated $100 million in losses
- Caesars Entertainment: Paid $15 million ransom after loyalty program data theft
UK Retail Sector (2024-2025):
- Marks & Spencer: Attack causing months of disruption, estimated to cost up to £300 million
- Harrods: Forced to shut down systems while maintaining operations
- Co-op: Internal systems compromised
Recent US Targets:
- Multiple insurance companies including Aflac, Philadelphia Insurance Companies, and Erie Insurance
- Airlines including potential links to Hawaiian Airlines and WestJet attacks
Law Enforcement Response and Investigation
Deputy Director Paul Foster, head of the NCA's National Cyber Crime Unit, emphasized the significance of the charges: "This attack caused significant disruption and millions in losses to TfL, part of the UK's critical national infrastructure."
The investigation represents unprecedented international cooperation, involving:
- UK National Crime Agency (NCA)
- City of London Police
- West Midlands Regional Organised Crime Unit
- British Transport Police
- FBI and US Department of Justice
- Crown Prosecution Service
"Earlier this year, the NCA warned of an increase in the threat from cyber criminals based in the UK and other English-speaking countries, of which Scattered Spider is a clear example. The NCA, UK policing and our international partners, including the FBI, are collectively committed to identifying offenders within these networks and ensuring they face justice."
The Social Engineering Playbook
What makes Scattered Spider particularly effective is their sophisticated understanding of human psychology and organizational processes. Their typical attack pattern involves:
- Target Research: Gathering intelligence on employees through social media and public sources
- Help Desk Infiltration: SCATTERED SPIDER operators routinely accurately respond to help desk verification questions when impersonating legitimate employees in calls made to request password and/or multifactor authentication (MFA) resets
- Credential Harvesting: Using social engineering to bypass traditional security measures
- Cloud Environment Compromise: SCATTERED SPIDER typically pivots from compromised Entra ID, SSO, and VDI accounts to integrated software-as-a-service (SaaS) applications
- Data Exfiltration and Extortion: Stealing sensitive data and demanding ransom payments
Industry Impact and Response
The arrest of these two teenagers has sent shockwaves through the cybersecurity community. "Since the recent arrests tied to the alleged Scattered Spider (UNC3944) members in the UK, Mandiant Consulting hasn't observed any new intrusions directly attributable to this specific threat actor", providing organizations with a crucial window to reassess their defenses.
However, experts warn that the threat is far from over. Authorities estimate that it may have as many as 1,000 members, and the decentralized nature of the group means that new actors regularly emerge to replace those who are arrested.
Defensive Strategies Against Social Engineering
The TfL attack underscores the critical need for organizations to evolve their security strategies beyond traditional technical controls:
Immediate Actions:
- Phishing-Resistant MFA: Implement hardware-based authentication like FIDO2 security keys
- Enhanced Verification Procedures: Require callback verification and managerial approval for sensitive actions
- Help Desk Training: Educate support staff about social engineering tactics
- Identity Monitoring: Deploy comprehensive logging and monitoring of identity systems
Long-term Strategy:
- Purple Team Exercises: Conduct regular simulations of social engineering attacks
- Zero Trust Architecture: Implement comprehensive identity and access management
- Third-Party Risk Assessment: Evaluate and monitor all vendor relationships
- Incident Response Planning: Prepare for identity-based compromise scenarios
The Future of Cybercrime
The Scattered Spider phenomenon represents a fundamental shift in the cybercrime landscape. These attackers aren't hacking the cloud — they're logging in, and by any means necessary. This evolution from technical exploitation to psychological manipulation has profound implications for how organizations must defend themselves.
As the group refines its operations, we anticipate the adoption of deepfake AI voice technology to impersonate employees and leadership roles, reducing the need to recruit human social engineers, suggesting that the threat will only become more sophisticated over time.

Legal Proceedings and Next Steps
Both defendants have been remanded in custody and are scheduled to appear at Southwark Crown Court on October 16. The case represents a significant test of international cooperation in cybercrime prosecution and could set important precedents for how authorities handle similar cases in the future.
The charges also highlight the serious legal consequences facing young cybercriminals. What may start as teenage hacking can quickly escalate into international criminal enterprises with severe penalties – Jubair potentially faces nearly a century in prison if convicted on all charges.
Conclusion: A Wake-Up Call for Critical Infrastructure
The TfL attack serves as a stark reminder that critical infrastructure operators face unprecedented threats from sophisticated adversaries who understand that the human element remains the weakest link in cybersecurity. While the arrests of Flowers and Jubair represent a significant victory for law enforcement, the broader Scattered Spider threat remains active and evolving.
Organizations must recognize that traditional perimeter defenses are insufficient against adversaries who specialize in social engineering and identity compromise. The future of cybersecurity lies not just in better technology, but in comprehensive approaches that address the human factors that make these attacks possible.
As Paul Foster of the NCA noted, this investigation demonstrates what can be achieved when victims are empowered to come forward and report incidents. The transparency and cooperation shown by TfL in this case should serve as a model for other organizations facing similar threats.
The battle against groups like Scattered Spider requires sustained international cooperation, continued investment in defensive capabilities, and a fundamental rethinking of how we protect our most critical digital infrastructure. The £39 million cost of the TfL attack is not just a financial figure – it's a down payment on the much larger investments needed to secure our increasingly connected world.
This article is based on official statements from the UK National Crime Agency, Crown Prosecution Service, and US Department of Justice, along with court proceedings and cybersecurity industry analysis. The case remains ongoing, and readers should be aware of contempt of court laws regarding active legal proceedings.









