UPenn Email System Compromised: Hackers Send Inflammatory Messages Threatening FERPA Data Leak

Date: November 1, 2025
Location: Philadelphia, PA
Incident Type: Email System Compromise / Marketing Platform Security Incident
Severity: High
Executive Summary
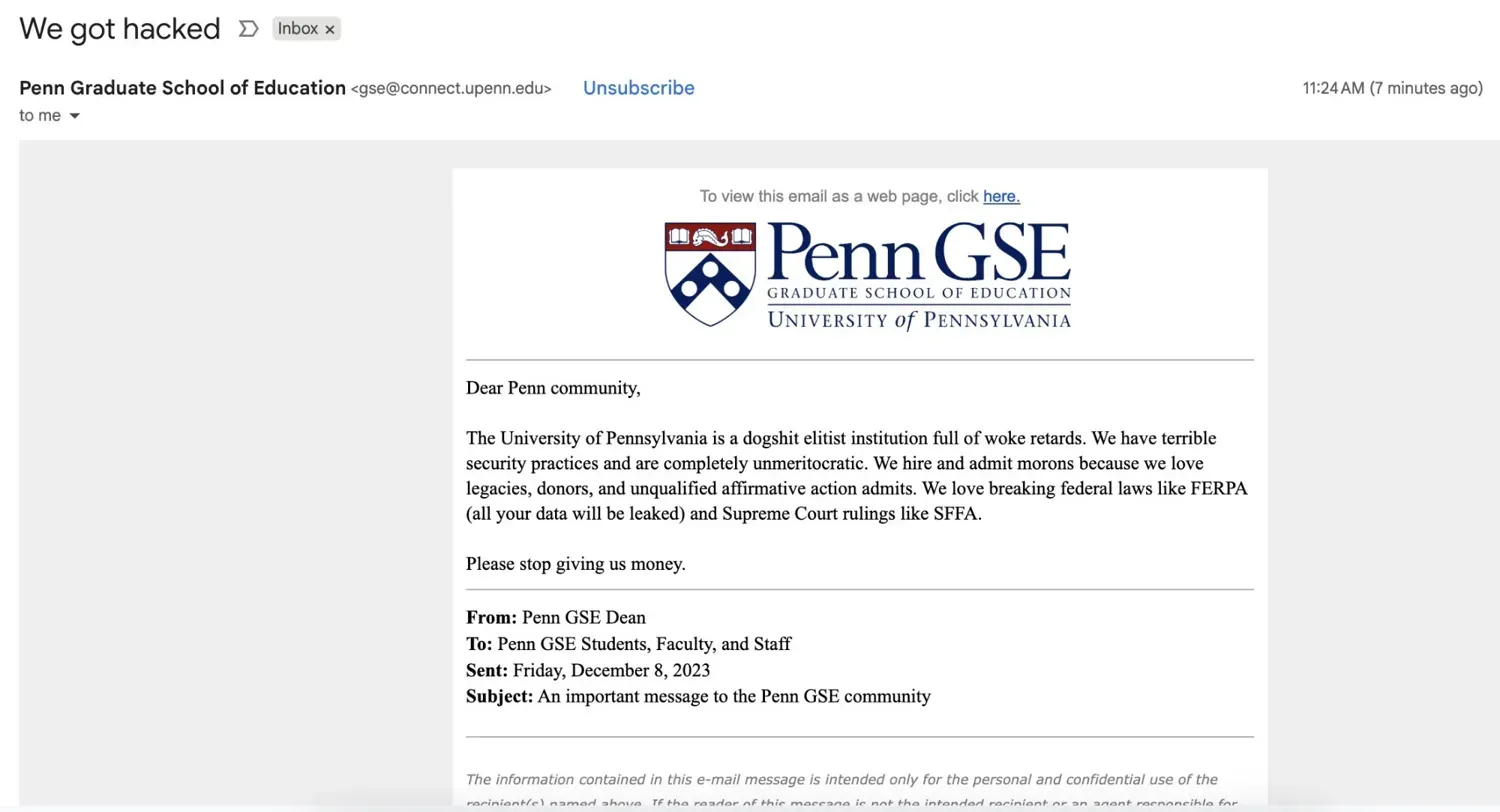
The University of Pennsylvania experienced a significant email security incident on October 31, 2025, when threat actors gained access to the institution's Salesforce Marketing Cloud platform and sent inflammatory mass emails to thousands of students, alumni, faculty, and staff. The emails, which appeared to originate from legitimate UPenn email addresses including the Graduate School of Education ([email protected]), contained offensive language and threatened to leak sensitive student data protected under FERPA regulations.
Incident Timeline
October 31, 2025 - Morning: Multiple waves of emails with the subject line "We got hacked (Action Required)" were sent from various Penn-affiliated email addresses to current students, alumni, faculty, staff, and community affiliates. Recipients reported receiving the message multiple times from different official @upenn.edu addresses.
October 31, 2025 - Afternoon: The university issued statements via Facebook and official channels acknowledging the incident, calling the emails "fraudulent" and "obviously fake." Penn's Office of Information Security and Incident Response team began investigating the compromise.
Technical Analysis
Attack Vector
The compromise appears to have involved UPenn's Salesforce Marketing Cloud infrastructure, specifically the "connect.upenn.edu" domain used for mass communications and alumni relations. Technical analysis by BleepingComputer confirmed that all malicious emails were routed through this platform, suggesting either:
- Direct compromise of UPenn's Salesforce Marketing Cloud account credentials
- Email spoofing leveraging the marketing platform's legitimate sending capabilities
- Exploitation of an unpatched vulnerability in the marketing automation system
Notably, the emails were sent from multiple different email addresses associated with various university departments, including the Graduate School of Education and purportedly from senior staff members, indicating the attackers had access to extensive mailing lists and sender configurations.
Email Content Analysis
The threatening emails contained several key elements:
- Inflammatory rhetoric targeting the university's admissions practices and security posture
- FERPA threat: Explicit claims that "all your data will be leaked" in reference to the Family Educational Rights and Privacy Act, which protects student education records
- SFFA reference: Mention of Students for Fair Admissions, referencing the 2023 Supreme Court ruling that struck down race-based affirmative action in college admissions
- Fundraising disruption: Request to "stop giving us money," potentially aimed at disrupting the university's development and alumni relations operations
Critically, university IT officials confirmed that the emails contained no malicious links or malware attachments, classifying this as primarily a reputational attack and social engineering campaign rather than a traditional malware distribution operation.
Pattern Recognition: Part of Larger Campaign
This incident fits into a broader pattern of politically-motivated cyberattacks targeting elite universities in the wake of the Supreme Court's 2023 affirmative action ruling. Similar attacks have recently targeted:
- Columbia University (August 2025): Data breach exposing sensitive information of over 860,000 individuals, with the attacker providing data to conservative activists
- University of Minnesota: Hacker explicitly stated goal was to prove continued non-compliance with Supreme Court ruling
- New York University: Similar breach with claims about continued race-based admissions
The coordinated nature and ideological messaging suggest these attacks may be part of an organized campaign rather than isolated incidents.
Political Context
The timing of the UPenn attack is particularly noteworthy:
- UPenn recently declined to sign the Trump administration's "Compact for Academic Excellence in Higher Education"
- The compact demanded universities accept government definitions of gender for campus facilities, eliminate demographic considerations in admissions, and require standardized testing
- The attack occurred one day after Pennsylvania Governor Josh Shapiro announced a collaboration with UPenn on AI policy guidance
- Several universities that refused the compact have subsequently experienced cyberattacks
Security Implications
Salesforce Marketing Cloud Vulnerabilities
This incident highlights several critical security concerns for organizations using Salesforce Marketing Cloud and similar marketing automation platforms:
- Third-party platform risk: Universities and enterprises often underestimate the security implications of marketing automation tools that have access to extensive contact databases and can send emails from legitimate organizational domains.
- Credential management: If the compromise resulted from stolen credentials, this underscores the critical need for multi-factor authentication (MFA) on all third-party marketing platforms, particularly those with mass communication capabilities.
- Email authentication gaps: Despite modern email authentication protocols (SPF, DKIM, DMARC), the attackers successfully sent emails that appeared legitimate enough to reach thousands of recipients, suggesting potential gaps in email authentication implementation.
- Supply chain attack surface: Marketing platforms represent a significant attack surface as they integrate with core institutional systems and have broad access to stakeholder contact information.
Higher Education Sector Vulnerabilities
Universities face unique cybersecurity challenges:
- Large, distributed user populations with varying security awareness levels
- Extensive third-party integrations for admissions, fundraising, and communications
- High-value data targets including research data, student records, and donor information
- Public-facing infrastructure required for accessibility and outreach
- Limited security budgets relative to the size and complexity of IT environments
Threat Actor Motivations
While attribution remains unclear, the attack demonstrates several possible motivations:
- Hacktivism: The political messaging suggests ideological motivation related to DEI policies and affirmative action
- Extortion preparation: The FERPA data leak threat may precede a ransomware or extortion demand
- Reputational damage: Disruption of fundraising and alumni relations during a critical period
- Political retaliation: Potential connection to UPenn's refusal to sign the White House education compact
Response and Mitigation
Institutional Response
The University of Pennsylvania's response included:
- Immediate public statements via Facebook and official channels acknowledging the incident
- Incident Response team activation from the Office of Information Security
- Communications to IT administrators explaining the incident contained no malware
- Ongoing investigation into the scope and method of compromise
However, the university has not yet disclosed:
- Whether actual data exfiltration occurred beyond email list access
- The specific vulnerability or compromise method
- Timeline for system restoration and security hardening
- Whether FERPA notification requirements will be triggered
Recommended Security Measures
Organizations using Salesforce Marketing Cloud or similar platforms should immediately:
- Implement MFA on all marketing platform accounts, especially those with send permissions
- Conduct access reviews of all users with email sending capabilities
- Review API integrations and connected applications for suspicious activity
- Audit email authentication (SPF, DKIM, DMARC) configurations to prevent domain spoofing
- Implement anomaly detection for unusual email sending patterns or volume spikes
- Segment email lists to limit potential exposure if credentials are compromised
- Establish rate limits on bulk sending operations
- Deploy email content filtering to detect and block messages containing suspicious keywords or patterns
- Create incident response playbooks specifically for marketing platform compromises
- Consider IP allowlisting to restrict platform access to known institutional networks
Data Leak Risk Assessment
As of this publication, no evidence has emerged of actual FERPA-protected data being leaked. However, the threat should be taken seriously for several reasons:
- Access to mailing lists confirms the attackers had some level of data access
- Multiple sender addresses suggests deeper platform penetration than simple credential theft
- Similar attacks have resulted in data leaks: The Columbia University incident resulted in actual data exposure
- FERPA violations carry significant penalties including loss of federal funding
UPenn students and alumni should monitor for:
- Identity theft indicators including credit monitoring alerts
- Targeted phishing campaigns using information from university databases
- Social engineering attacks leveraging knowledge of educational history
- Future extortion attempts if the data leak threat materializes
Industry-Wide Implications
This incident serves as a critical warning for the higher education sector:
- Marketing platforms are high-value targets that attackers increasingly recognize as vulnerable entry points
- Political climate creates new threat vectors for institutions taking positions on controversial issues
- Email remains a critical vulnerability despite decades of security investments
- Third-party risk management must include regular security assessments of all platforms with mass communication capabilities
- Incident response plans must account for reputational attacks, not just traditional cybercrime
Ongoing Developments
This remains a developing situation. Key questions to monitor:
- Will the threatened FERPA data leak materialize?
- What was the specific attack vector used to compromise the Salesforce platform?
- Will similar attacks target other universities that declined the White House compact?
- What regulatory consequences will UPenn face if actual data exposure is confirmed?
- How will this incident impact university email security practices industry-wide?
Recommendations for UPenn Community
Current and former UPenn students, faculty, and staff should:
- Monitor financial accounts for signs of identity theft
- Enable credit monitoring if available through university resources
- Be alert for targeted phishing using university-specific information
- Update passwords for UPenn systems and any accounts using similar credentials
- Report suspicious communications to [email protected]
- Document any suspicious activity related to their UPenn affiliation
Conclusion
The University of Pennsylvania email incident represents a convergence of technical vulnerabilities, political tensions, and evolving attack methodologies. The compromise of a legitimate marketing automation platform to send mass communications highlights a critical gap in many organizations' security postures: third-party platforms with extensive access and trust are increasingly being weaponized by threat actors.
For the higher education sector specifically, this incident underscores the need for enhanced security around all systems that can communicate with stakeholder populations at scale. As universities navigate an increasingly politicized landscape, they must anticipate that traditional cybersecurity threats will increasingly blend with hacktivism and ideologically-motivated attacks.
The threatened FERPA data leak, if it materializes, could trigger significant regulatory consequences and further damage institutional trust. However, even if no data is ultimately leaked, the reputational impact and operational disruption demonstrate that modern cyberattacks increasingly target organizational credibility as much as technical infrastructure.
Organizations across all sectors should use this incident as a catalyst to review their third-party platform security, particularly any systems with mass communication capabilities, and ensure that marketing automation tools receive the same security scrutiny as critical infrastructure.
Update Policy: This article will be updated as new information becomes available about the scope of the compromise, potential data exposure, and attribution.
Contact: For tips or information related to this incident, contact the editorial team at contact information for breached.company
Source Verification: All information in this article has been verified against multiple reputable cybersecurity and news sources, including BleepingComputer, TechCrunch, Fox News Digital, The Record, and official university statements.





