Corporate Security Alert: How Human Trafficking Networks Are Targeting Businesses Through Digital Exploitation

Critical Threat Assessment for Corporate Leaders
Recent global law enforcement operations have revealed a disturbing trend: human trafficking networks are increasingly targeting corporate environments through sophisticated digital exploitation schemes. As businesses continue to expand their digital footprint, understanding these threats has become essential for protecting both your organization and your employees.
The Business Connection: Why Companies Are Targets
Supply Chain Vulnerabilities
Federal contractors are now required to certify that their supply chains have not engaged in trafficking-related activities for contracts exceeding $500,000. The Department of Labor's enhanced rules specifically target companies to ensure they have protections in place against labor trafficking throughout their operations.
Employee Recruitment Scams
Human trafficking networks are using fake job advertisements to target professionals, particularly those with technical backgrounds or language skills. These sophisticated schemes often:
- Target employees through LinkedIn and professional networking sites
- Offer high-salary positions with remote work opportunities
- Request extensive personal information during "background checks"
- Use legitimate-looking company branding and websites
www.myprivacy.blog/major-sex-trafficking-takedowns-2024-2025-a-global-crackdown-on-digital-exploitation/
Financial Exploitation Through Employee Targeting
The recent Europol takedown of a $540 million cryptocurrency fraud network demonstrates how traffickers use corporate environments to legitimize their operations, often recruiting employees unknowingly into money laundering schemes.

Recent Operations: What Businesses Need to Know
Operation Restore Justice Findings
The April 2025 FBI operation that arrested 205 offenders revealed critical insights for corporate security:
- Trusted Position Infiltration: Arrests included individuals in positions of public trust—law enforcement, military personnel, and teachers
- Technology Exploitation: Predators used corporate communication tools and platforms to facilitate crimes
- Cross-Border Operations: International coordination was essential for successful prosecutions

Digital Infrastructure Targeting
INTERPOL's Operation Synergia identified over 1,300 malicious servers used by trafficking networks, many hosted by legitimate web hosting providers. This highlights how criminals exploit legitimate business infrastructure.
Corporate Communication Compromises
The takedown of the MATRIX encrypted messaging service in December 2024 revealed how trafficking networks use sophisticated communication tools that may resemble legitimate business applications.
Industry-Specific Threat Vectors
Technology Companies
- Platform Exploitation: The 764 Network case demonstrates how gaming platforms and social media can be exploited
- AI Misuse: Traffickers are using AI to create convincing fake job advertisements and deepfake technology for exploitation
- Cryptocurrency Integration: Fraud operations increasingly use crypto platforms for money laundering
Transportation and Logistics
The Department of Transportation compiled guidance for transportation organizations, while DHS developed human trafficking awareness tutorials for ride-share drivers, indicating heightened risks in these sectors.

Financial Services
Between July and December 2023, Operation HAECHI-IV targeted financial criminals across 34 countries, arresting 3,500 suspects and seizing over $300 million, demonstrating how trafficking networks exploit financial infrastructure.
Hospitality and Service Industries
Operations Global Chain identified numerous cases where massage parlours, hotels, and service businesses were used as fronts for trafficking operations.
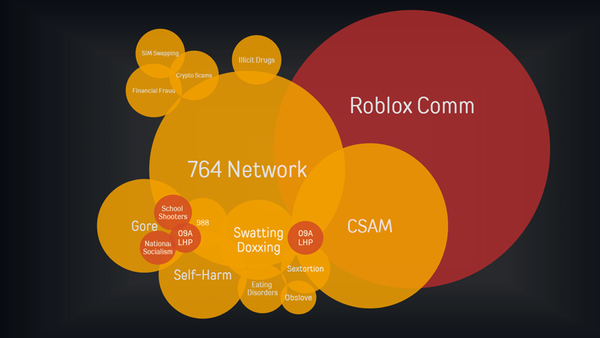
Red Flags for Corporate Security Teams
Recruitment and HR Warnings
- Unusually High-Paying Remote Positions: Especially those requiring minimal qualifications
- Requests for Passport/ID Documents: Before formal employment begins
- Pressure for Quick Decisions: Legitimate offers typically allow consideration time
- Vague Job Descriptions: Particularly for "digital sales" or "customer service" roles

Financial Transaction Indicators
- Unusual Payment Methods: Cryptocurrency-only transactions or unusual banking arrangements
- High-Volume Cash Transactions: Particularly in service industries
- Multiple Account Transfers: Rapid movement of funds between accounts
- International Wire Transfers: To high-risk jurisdictions
Digital Infrastructure Concerns
- Suspicious Communication Platforms: Encrypted messaging apps not standard for business use
- Unusual Server Requests: Hosting requirements that don't match business needs
- Anonymous Domain Registrations: Websites registered with privacy protection services
Corporate Protection Strategies
Employee Education and Awareness
Mandatory Training Programs: Implement comprehensive training covering:
- Recognition of recruitment scams
- Safe online communication practices
- Reporting procedures for suspicious activities
- Understanding of company policies regarding external communications
Regular Security Briefings: Keep employees informed about emerging threats and recent law enforcement findings.

Technical Security Measures
Network Monitoring: Implement advanced monitoring to detect:
- Unusual communication patterns
- Access to known malicious IP addresses
- Large file transfers or data exfiltration attempts
- Connections to known trafficking-related infrastructure
Email and Communication Security:
- Advanced spam and phishing filters
- Monitoring of job posting platforms for fake listings using company names
- Regular audits of official company communication channels
Supply Chain Due Diligence
Enhanced Vendor Screening:
- Verify business licenses and registrations
- Check against international watchlists
- Review labor practices and working conditions
- Implement regular compliance audits
Contract Requirements:
- Include specific anti-trafficking clauses
- Require certification of compliance with trafficking laws
- Establish clear reporting procedures for violations
Partnership with Law Enforcement
Information Sharing: Establish relationships with:
- Local FBI field offices
- INTERPOL National Central Bureau
- Industry-specific task forces
- Private sector security consortiums
Incident Reporting: Develop clear procedures for reporting suspected trafficking activities to appropriate authorities.
Legal and Compliance Considerations
Federal Requirements
Companies must understand their obligations under:
- Trafficking Victims Protection Act (TVPA): Particularly for federal contractors
- Customs and Facilitations and Trade Enforcement Act: Regarding imported goods
- Enhanced reporting requirements: Under the REPORT Act signed in 2024
International Compliance
For multinational corporations, compliance with:
- EU Anti-Trafficking Directive: Adopted May 2024
- Local jurisdiction requirements: Varying by country of operation
- Supply chain transparency laws: Increasingly common globally

Documentation and Record-Keeping
Maintain comprehensive records of:
- Employee screening procedures
- Vendor due diligence processes
- Training program completion
- Incident reports and responses
Incident Response Procedures
Immediate Response Protocol
- Secure the Environment: Isolate affected systems and preserve evidence
- Contact Authorities: FBI (1-800-CALL-FBI) and local law enforcement
- Document Everything: Maintain detailed records of all activities
- Notify Stakeholders: According to established communication plans
- Legal Consultation: Engage experienced counsel immediately
Long-term Recovery
- Comprehensive Security Review: Assess and update all security measures
- Employee Support: Provide counseling and support for affected personnel
- Process Improvement: Update policies and procedures based on lessons learned
- Ongoing Monitoring: Enhanced vigilance for related threats
Technology Solutions and Best Practices
AI-Powered Detection
Implement AI tools for:
- Anomaly Detection: Identify unusual patterns in communications and transactions
- Content Analysis: Screen job postings and communications for trafficking indicators
- Risk Assessment: Automated evaluation of vendor and partner risk profiles
Blockchain and Verification
Use blockchain technology for:
- Supply Chain Verification: Immutable records of product origin and handling
- Document Authentication: Verify the authenticity of credentials and certifications
- Transaction Tracking: Enhanced visibility into financial flows
Building a Corporate Anti-Trafficking Program
Executive Leadership
Successful programs require:
- C-Suite Commitment: Visible leadership support and resource allocation
- Cross-Functional Teams: Security, HR, Legal, and Operations coordination
- Regular Assessment: Quarterly reviews of program effectiveness
- External Expertise: Consultation with anti-trafficking specialists
Metrics and Measurement
Track key performance indicators:
- Training Completion Rates: Percentage of employees completing awareness training
- Incident Detection Time: Speed of identifying and responding to threats
- Vendor Compliance: Percentage of suppliers meeting anti-trafficking standards
- Reporting Volume: Number of suspicious activities reported by employees
Industry Collaboration and Information Sharing
Sector-Specific Initiatives
Participate in industry groups such as:
- Technology Coalition: For tech companies addressing online exploitation
- Financial Services: Anti-money laundering and fraud prevention groups
- Transportation: Awareness and prevention programs
- Manufacturing: Supply chain integrity initiatives
Public-Private Partnerships
Engage with:
- National Human Trafficking Hotline: 1-888-373-7888
- Department of Homeland Security: Blue Campaign resources
- FBI InfraGard: Private sector partnership program
- INTERPOL Global Complex: Business engagement initiatives
Conclusion: Building Resilience Against Trafficking Threats
The recent wave of global law enforcement operations demonstrates both the scale of the trafficking threat and the effectiveness of coordinated response efforts. For businesses, the message is clear: trafficking networks are sophisticated, well-funded, and increasingly targeting corporate environments.
However, companies that implement comprehensive anti-trafficking programs can significantly reduce their risk exposure while contributing to global efforts to combat this crime. The investment in prevention is far smaller than the potential costs of involvement in trafficking operations, whether intentional or inadvertent.
By staying informed about emerging threats, implementing robust security measures, and maintaining strong partnerships with law enforcement and industry peers, businesses can protect themselves while supporting the broader fight against human trafficking.
Remember: trafficking networks rely on the anonymity and legitimacy that corporate environments provide. By implementing the measures outlined in this assessment, your organization becomes a less attractive target and a stronger ally in the global fight against exploitation.
Immediate Action Items:
- Review and update employee recruitment procedures
- Conduct comprehensive supply chain assessment
- Implement enhanced communication monitoring
- Establish relationships with local law enforcement
- Schedule quarterly anti-trafficking training for all personnel
For Additional Resources:
- FBI Human Trafficking Tips: tips.fbi.gov
- National Human Trafficking Hotline: 1-888-373-7888
- DHS Blue Campaign: dhs.gov/blue-campaign
- INTERPOL Business Engagement: interpol.int/private-sector














