Global Cybercrime Crackdown 2025: A Mid-Year Assessment of Major Arrests and Takedowns

As we reach the end of August 2025, law enforcement agencies worldwide have achieved unprecedented success in dismantling cybercriminal networks, marking this as potentially the most successful year in the fight against cybercrime to date.
Executive Summary
The first eight months of 2025 have witnessed an extraordinary surge in international law enforcement cooperation against cybercrime, resulting in hundreds of arrests, the seizure of millions in cryptocurrency, and the disruption of major criminal infrastructure across the globe. From sophisticated ransomware operations to massive botnet networks, authorities have struck decisive blows against the cybercriminal ecosystem.

Key Statistics:
- Over 1,000 arrests globally
- More than €75 million in cryptocurrency and assets seized
- Hundreds of servers and thousands of domains taken down
- Multiple major ransomware operations disrupted
- Billions of stolen credentials recovered from infostealer operations

Major International Operations
Operation Endgame: The Largest Botnet Takedown in History
Timeline: May 2024 - Ongoing through 2025
Operation Endgame stands as the crown jewel of 2025's cybercrime enforcement efforts. Initially launched in May 2024, this operation has continued throughout 2025 with multiple phases targeting the foundational infrastructure of cybercrime.
Phase 1 (May 2024):
- Disrupted major malware "droppers" including IcedID, SystemBC, Pikabot, Smokeloader, and Bumblebee
- 4 arrests in Ukraine and Armenia
- Over 100 servers taken down worldwide
- More than 2,000 domains seized
- One suspect earned at least €70 million from renting infrastructure for ransomware attacks
2025 Follow-up Operations:
- May 2025: Law enforcement dismantled approximately 300 servers and neutralized 650 domains
- €3.5 million in cryptocurrency seized, bringing total Operation Endgame seizures to over €21.2 million
- International arrest warrants issued for 20 key cybercriminals
- Targeted new malware variants including Bumblebee, Lactrodectus, QakBot, HijackLoader, DanaBot, TrickBot, and WARMCOOKIE
April 2025 Customer Arrests:
- 5 individuals detained and interrogated
- Focused on customers of the Smokeloader botnet
- Several suspects cooperated with authorities, allowing examination of digital evidence
- Database seizures enabled linking online personas to real identities

Operation Secure: Asian Infrastructure Crackdown
Timeline: January - April 2025
This massive Asian operation demonstrated unprecedented regional cooperation in combating cybercrime.
Key Results:
- 32 arrests across Vietnam (18), Sri Lanka (12), and Nauru (2)
- 41 physical servers seized
- Over 100 GB of criminal data recovered
- More than 20,500 malicious IPs and domains taken down
- 216,000+ victims identified
- 69 infostealer variants investigated including Lumma, Risepro, and Meta Stealer
Participating Countries: 26 nations including Vietnam, Sri Lanka, Nauru, Hong Kong, India, Indonesia, Japan, Malaysia, Philippines, Singapore, Thailand, and others.

Operation Red Card: African Cybercrime Elimination
Timeline: November 2024 - February 2025
This operation specifically targeted cross-border criminal networks affecting African nations and their international victims.
Major Achievements:
- Over 300 arrests across 7 African countries
- More than 5,000 victims identified
- Focus on mobile banking, investment, and messaging app scams
- Nigeria: 130 arrests including 113 foreign nationals involved in online casino and investment fraud
- South Africa: 40 arrests with seizure of 1,000+ SIM cards and 53 computers in SIM box fraud scheme
- Rwanda: 45 arrests in social engineering scams
- Zambia: 14 arrests in phone hacking syndicate
Participating Countries: Benin, Côte d'Ivoire, Nigeria, Rwanda, South Africa, Togo, and Zambia.

Operation Magnus: RedLine and Meta Infostealer Takedown
Timeline: October 28, 2024 - Continuing into 2025
One of the most significant infostealer disruptions in cybercrime history, targeting two of the world's most prolific credential theft operations.
Major Results:
- Complete infrastructure seizure with "full access" to all RedLine and Meta servers
- US Charges: Maxim Rudometov charged with access device fraud, conspiracy to commit computer intrusion, and money laundering (facing up to 35 years in prison)
- Belgian Arrests: 2 individuals arrested, one remains in custody
- Infrastructure Impact: All source code obtained, license servers, REST-API servers, panels, stealers, and Telegram bots seized
- Victim Scale: Over 1 billion credentials stolen since RedLine's 2020 launch, with 227 million unique email/password pairs stolen in 2024 alone
Law Enforcement Tactics: Dutch Police created accounts on Russian cybercrime forums, sending direct warning messages to criminals stating "This is an official notice from law enforcement"
Participating Agencies: Dutch National Police, FBI, UK NCA, Australian Federal Police, Portuguese Federal Police, Eurojust, and others.
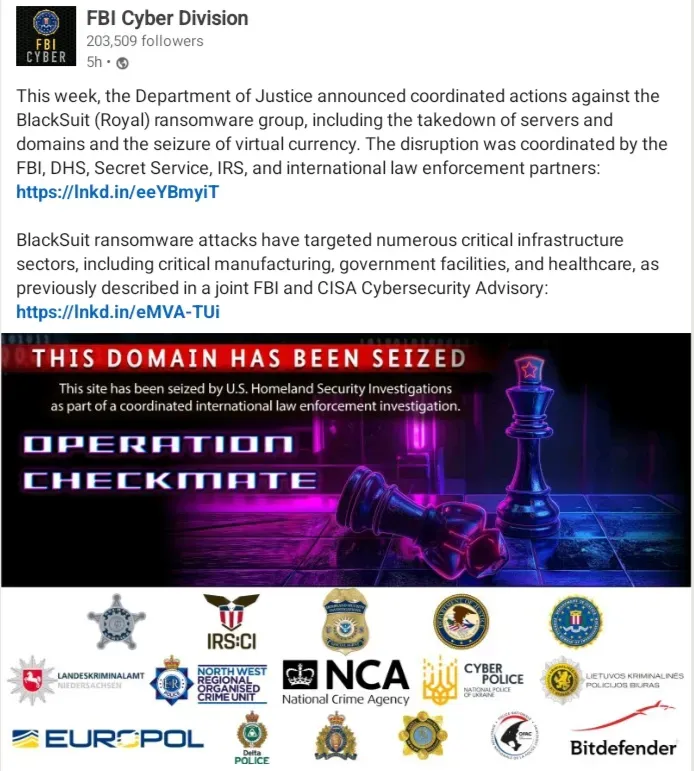
Operation Checkmate: BlackSuit/Royal Ransomware Destruction
Timeline: July 24, 2025
A devastating blow to one of the world's most destructive ransomware operations, which had evolved from the notorious Conti group.
Unprecedented Impact:
- Financial Scope: Over $370 million in ransom payments collected since 2022
- Victim Count: More than 450 US organizations compromised, including healthcare, education, energy, and government sectors
- Infrastructure Seized: 4 servers, 9 domains, and $1.09 million in cryptocurrency
- Critical Sectors Targeted: Healthcare systems, causing direct threats to patient safety
Post-Takedown Evolution: Evidence suggests former BlackSuit members formed new "Chaos" ransomware group, demonstrating the adaptive nature of cybercriminal networks
International Coordination: Led by US Homeland Security Investigations with partners from UK, Germany, Ireland, Ukraine, and Netherlands.
Operation RapTor: Dark Web Marketplace Disruption
Timeline: May 2025
Building on previous dark web enforcement successes, this operation achieved record-breaking results.
Global Impact:
- 270 arrests across 10 countries
- Country Breakdown: United States (130), Germany (42), United Kingdom (37), France (29), South Korea (19), Austria (4), Netherlands (4), Brazil (3), Switzerland (1), Spain (1)
- Over $200 million in currency and digital assets seized
- More than 2 metric tons of drugs recovered
- 144 kilograms of fentanyl or fentanyl-laced narcotics
- Over 180 firearms seized
Marketplaces Targeted: Nemesis, Tor2Door, Bohemia, and Kingdom Markets.
High-Profile Individual Cases
Scattered Spider Leadership Crackdown
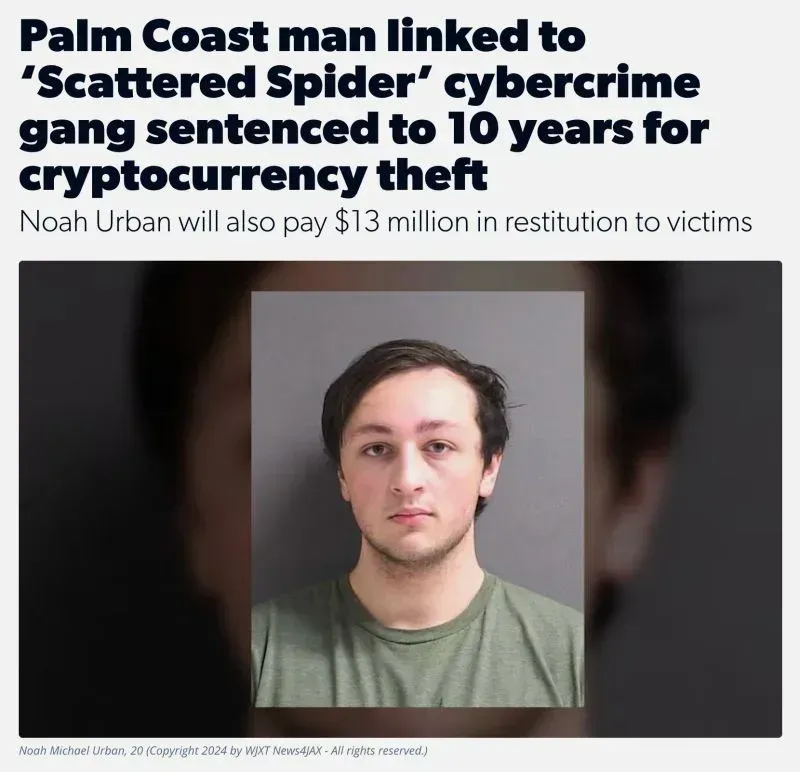
Key Figure: Noah Urban, 20, Palm Coast, Florida
- Sentence: 10 years in federal prison (August 2025)
- Restitution: $13 million to 59 victims
- Role: First Scattered Spider member to be sentenced
- Assets Forfeited: Multiple cryptocurrencies worth millions, cash, jewelry, and watches
Other Co-Defendants:
- Tyler Robert Buchanan, 22: Alleged leader from Scotland, extradited from Spain after arrest in Palma de Mallorca
- Ahmed Hossam Eldin Elbadawy, 23: Texas-based, whereabouts unknown
- Joel Martin Evans, 25: North Carolina, arrested November 2024
- Evans Onyeaka Osiebo, 20: Dallas, whereabouts unknown
911 S5 Botnet Mastermind
Key Figure: YunHe Wang
- Arrest: May 2025
- Operation: Created and operated 911 S5 residential proxy service
- Scale: Compromised millions of residential Windows computers with 19+ million unique IP addresses
- Revenue: Approximately $99 million from 2018-2022
- Usage: Facilitated financial crimes, stalking, bomb threats, child exploitation, and export violations

Phobos and 8Base Ransomware Networks
Major Developments:
- June 2024: Phobos administrator arrested in South Korea, extradited to US in November
- 2025: Four Russian nationals leading 8Base ransomware group arrested
- Italy: Key Phobos affiliate arrested
- Both groups identified as among the most active ransomware operators of 2024
Regional Enforcement Highlights
European Union Operations
Operation Synergia (Phase 2):
- Timeline: April 1 - August 31, 2025
- Results: 41 arrests, 43 devices seized, 65 individuals under investigation
- Infrastructure: 22,000+ malicious IP addresses taken down (75% of identified targets)
- Participation: 95 Interpol member countries
Russian Domestic Enforcement
Notable Change in Policy:
- October 2024: Four REvil gang members sentenced to prison
- November 2024: Mikhail Matveev arrested (wanted by FBI since 2023 for Hive and LockBit involvement)
- December 2024: Russian national sentenced to 20 years for Netwalker ransomware
- Signals shift in Russia's relationship with cybercriminals
Operation Destabilise: Money Laundering Network Disruption
Timeline: December 2024
A major blow to cryptocurrency laundering operations supporting ransomware groups.
Key Results:
- 84 arrests across multiple countries
- Over $25 million in illicit funds seized
- Network responsible for laundering Ryuk ransomware profits
- Exposed cash-for-crypto trading schemes between Western organized crime and cybercriminals
United Kingdom Actions
Recent Operations:
- July 2025: Four arrests for ransomware attacks on M&S, Co-op, and Harrods
- Continued leadership in international cooperation efforts
- Major role in LockBit takedown operations
Additional Notable Arrests and Cases
Seventh Scattered Spider Member:
- December 2024: Remington Goy Ogletree, 19, from Texas arrested
- Represents continued pressure on the notorious social engineering group
Military Personnel Cybercrime:
- December 31, 2024: US soldier arrested for allegedly hacking AT&T and Verizon systems
- Highlights cybercrime infiltration across all sectors
Extradition Successes:
- November 2024: Evgenii Ptitsyn extradited from South Korea to US for Phobos ransomware charges
- July 2025: Tyler Buchanan (Scattered Spider leader) extradited from Spain to US
- July 2025: Russian national extradited from Indonesia for Telegram data sales
Ransomware Ecosystem Disruption
Major Groups Affected
LockBit: Despite being the most prolific ransomware group with 526 observed attacks in 2024, suffered major disruption:
- Infrastructure seized and controllers exposed
- Leader "LockBitSupp" sanctioned
- Group has attempted comeback with LockBit 4.0
RansomHub: Emerged in February 2024 to fill LockBit void but mysteriously disappeared in April 2025
8Base, Babuk-Bjorka, FunkSec, BianLian, Cactus, Hunters International: All ceased operations in Q2 2025
Impact on Ransomware Landscape
Measurable Effects:
- 6% drop in victims listed on ransomware leak sites in Q2 2025
- Increased fragmentation of ransomware ecosystem
- Number of threat actors nearly doubled as groups splintered
- Shift from encryption-based to data theft extortion
Technology and Infrastructure Seizures
Cryptocurrency Recovery
Total Seized Globally: Over €75 million in various cryptocurrencies including:
- Bitcoin
- Ethereum
- Monero
- Dai
- Ripple
Notable Individual Seizures:
- Operation Endgame: €21.2 million total
- BlackSuit takedown: $1.09 million from single victim payment
- Operation Destabilise: $25 million in money laundering network
- Operation RapTor: Over $200 million in currency and digital assets
Server and Domain Takedowns
Operation Endgame Totals:
- Nearly 400 servers dismantled across all phases
- Over 2,650 domains neutralized
- Command-and-control infrastructure destroyed
Operation Secure Results:
- 41 physical servers seized
- 20,500+ malicious IPs and domains taken down
Emerging Trends and Challenges
Cybercriminal Adaptation
New Tactics Observed:
- Shift to smaller, single-vendor dark web shops
- Increased use of legitimate tools for malicious purposes
- Greater operational security awareness
- Migration to new ransomware-as-a-service platforms
Law Enforcement Evolution
Enhanced Capabilities:
- Improved international cooperation frameworks
- Better intelligence sharing mechanisms
- Advanced cryptocurrency tracing techniques
- Proactive infrastructure targeting
Geographic Shifts
Notable Changes:
- Increased African law enforcement participation
- Enhanced Asian regional cooperation
- Russian domestic enforcement actions
- Continued European leadership role
Private Sector Collaboration
Industry Partners
Cybersecurity Firms Contributing Intelligence:
- Group-IB
- Kaspersky
- Trend Micro
- CrowdStrike
- Various other security vendors
Financial Sector Cooperation:
- Enhanced cryptocurrency exchange monitoring
- Improved suspicious transaction reporting
- Better cross-border financial intelligence sharing
Looking Forward: Second Half of 2025
Projected Trends
Continued Enforcement Pressure:
- Additional Operation Endgame phases planned
- Expanded international cooperation frameworks
- Focus on cryptocurrency laundering networks
- Targeting of affiliate recruitment networks
Cybercriminal Response:
- Expected further fragmentation of major groups
- Increased operational security measures
- Migration to new technologies and platforms
- Potential shift to less detectable attack methods
Challenges Ahead
Persistent Issues:
- Rapid reconstitution of criminal networks
- Emergence of new threat actors
- Technological adaptation by criminals
- Jurisdictional and legal complexities
Conclusion
The first eight months of 2025 have demonstrated unprecedented success in global cybercrime enforcement, with over 1,000 arrests and the disruption of major criminal infrastructure worldwide. The scale and coordination of international operations like Endgame, Secure, Magnus, Checkmate, and RapTor represent a new paradigm in cybercrime fighting.
Key Success Factors:
- Enhanced international cooperation
- Improved intelligence sharing
- Advanced technical capabilities
- Sustained pressure campaigns
- Private sector collaboration
- Innovative psychological warfare tactics
Measurable Impact:
- Significant disruption to ransomware operations
- Fragmentation of major criminal networks
- Substantial financial losses for cybercriminals (over €75 million seized)
- Recovery of billions of stolen credentials
- Improved deterrent effect through high-profile arrests and extraditions
Game-Changing Developments:
- Operation Magnus exposed the scale of credential theft with over 1 billion stolen passwords recovered
- Operation Checkmate dismantled a $370 million ransomware empire
- Russian enforcement actions signal changing geopolitical dynamics
- Infostealer takedowns disrupted the foundational infrastructure of cybercrime
However, the cybercriminal ecosystem has shown remarkable resilience and adaptability. The rapid emergence of new groups like Chaos ransomware following BlackSuit's takedown, and the continued evolution of threat actor tactics, highlight the ongoing nature of this challenge.
Emerging Challenges:
- Rapid reconstitution of criminal networks under new brands
- Increased operational security awareness among criminals
- Migration to new technologies and attack vectors
- Evolution from encryption-based to data theft extortion models
As we move into the final months of 2025, law enforcement agencies worldwide continue to build on these successes, with additional operations planned and new international cooperation frameworks being developed. The implementation of innovative tactics—from psychological operations targeting criminal forums to coordinated financial asset seizures—demonstrates the evolution of law enforcement capabilities.
The message is clear: No corner of the internet is beyond the reach of determined, coordinated law enforcement action, and 2025 has set a new standard for what can be achieved when the global community works together against cybercrime. The year has proven that sustained international pressure, combined with advanced technical capabilities and private sector cooperation, can fundamentally disrupt even the most sophisticated cybercriminal enterprises.














