Global Cybercrime Crackdown: Major Law Enforcement Operations of 2024-2025

As digital crime continues to evolve in sophistication and scale, international law enforcement agencies have responded with increasingly coordinated global operations. These efforts have resulted in significant arrests, infrastructure takedowns, and the disruption of major cybercriminal networks. The period of 2024-2025 has seen some of the most impactful cybercrime operations in law enforcement history, with authorities around the world collaborating to combat ransomware groups, dark web marketplaces, and cross-border fraud networks.

Operation Red Card: Targeting African Cybercrime Networks
In one of the most recent major crackdowns, INTERPOL coordinated "Operation Red Card," a massive international effort targeting cybercriminal networks across Africa. Between November 2024 and February 2025, law enforcement authorities from seven African countries arrested 306 suspects and seized 1,842 devices allegedly used in various cybercrimes.
The operation specifically targeted mobile banking scams, fraudulent investment schemes, and messaging app scams linked to over 5,000 victims. Key participating countries included Benin, Côte d'Ivoire, Nigeria, Rwanda, South Africa, Togo, and Zambia.
Neal Jetton, INTERPOL's Director of the Cybercrime Directorate, emphasized the operation's significance, stating that it "demonstrates the power of international cooperation in combating cybercrime, which knows no borders and can have devastating effects on individuals and communities."
The operation's success was bolstered by intelligence sharing between countries and private sector partners, including cybersecurity firms Group-IB, Kaspersky, and Trend Micro.
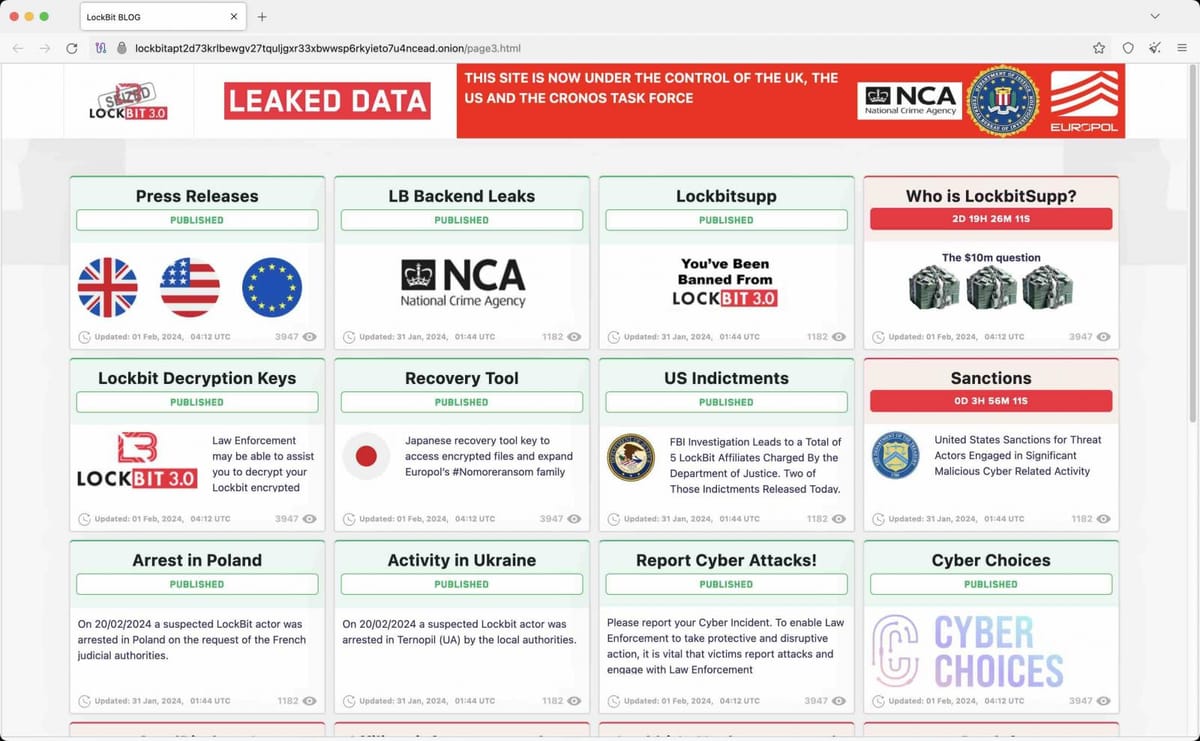
Operation Cronos: The LockBit Takedown
In February 2024, law enforcement agencies from 10 countries collaborated in "Operation Cronos" to dismantle LockBit, one of the most prolific ransomware gangs in history. Led by the UK's National Crime Agency (NCA) and the FBI, investigators managed to deeply compromise LockBit's infrastructure, gaining critical insights into their operations.
The operation yielded remarkable results:
- Over 1,000 LockBit ransomware decryption keys were obtained and provided to victims
- More than 200 cryptocurrency accounts linked to the group were frozen
- Multiple individuals associated with LockBit were arrested or indicted globally
- Law enforcement gained control of LockBit's data leak sites, using them to reveal information about the group's operations
Investigators discovered that despite promises to the contrary, LockBit did not delete victims' data after receiving ransom payments, revealing the group's dishonesty even in their criminal operations. This takedown represented a significant blow to the ransomware ecosystem, as LockBit had been one of the most active and destructive ransomware groups in recent years.

Operation Talent: Dismantling Cybercrime Marketplaces
In January 2025, international law enforcement agencies executed "Operation Talent," targeting a series of cybercrime-related websites that played crucial roles in the cybercriminal ecosystem. The operation focused on websites associated with Cracked, Nulled, StarkRDP, Sellix, and MySellix.
These platforms facilitated various cybercriminal activities, including:
- Trading in stolen login credentials
- Distributing pirated software
- Selling video game cheats
- Trafficking in stolen credit card information
The operation was coordinated by Europol with participation from multiple countries. The seizure notices posted on the affected websites indicated that the takedown included not only the websites themselves but also information on their customers and victims, potentially leading to further investigations and arrests.

Operation Moonlander: The Anyproxy and 5socks Botnets
As detailed in our previous article, "Operation Moonlander" successfully dismantled the Anyproxy and 5socks botnets in May 2025. This operation targeted a network of compromised routers that had been operating for nearly two decades, generating over $46 million in illicit profits.
The operation resulted in the indictment of four individuals – three Russian nationals and one Kazakhstani national – on charges related to operating the botnet services. The criminals had infected older-model wireless internet routers with a variant of TheMoon malware, allowing them to reconfigure devices and sell access to the compromised machines as proxy servers.

Operation Serengeti: Massive Arrests Across Africa
Between September and October 2024, another significant INTERPOL-coordinated operation dubbed "Operation Serengeti" led to the arrest of 1,006 suspects across 19 African countries. The operation targeted criminals behind ransomware, business email compromise (BEC), digital extortion, and online scams.
Law enforcement agencies dismantled over 134,000 malicious infrastructures and networks during the operation. More than 35,000 victims were identified, with cases linked to nearly $193 million in financial losses worldwide.
The operation's effectiveness was enhanced by intelligence-led actions focused on the most significant cybercriminal actors, with private sector partners including Internet Service Providers contributing to the effort.

The Fragmentation of Ransomware Groups
Following the takedown of LockBit in early 2024, cybersecurity experts observed a significant trend: the fragmentation of the ransomware landscape. Rather than a few dominant groups controlling large portions of the market, 2024-2025 saw the emergence of numerous smaller ransomware operations, each claiming a smaller share of victims.
As Ben Jones, Co-Founder and CEO at Searchlight Cyber, noted, "More ransomware groups [are operating] but with a smaller victim share, possibly operating on the hope that if they maintain a low-level of activity they can avoid the type of law enforcement action that LockBit encountered."
New ransomware groups that emerged or gained prominence in 2024-2025 include:
- RansomHub: Following the takedown of major competitors like LockBit and BlackCat (ALPHV), RansomHub quickly established itself as a leader in the Ransomware-as-a-Service (RaaS) market.
- Fog Ransomware: First appearing in April 2024, Fog targeted educational institutions predominantly in the United States, exploiting stolen VPN credentials to gain initial access.
- Lynx Ransomware: Another emerging threat in the fragmented ransomware landscape of 2025.

TheCom Ecosystem Takedowns
Law enforcement agencies made significant inroads against "TheCom," a broad online ecosystem of cybercriminals primarily composed of young individuals from Canada, the U.S., and the U.K. This network has been linked to high-profile threat groups including LAPSUS$, Roasting 0ktapus, Scattered Spider, and Octo Tempest.
Several arrests were made in 2024 targeting individuals associated with TheCom, including the apprehension of Noah Michael Urban (aka "Sosa," "Elijah," "King Bob"), who was linked to the Roasting 0ktapus group.
Despite these arrests, TheCom has proved resilient, with many of its members remaining active on messaging services and forums, highlighting the persistent challenge faced by law enforcement in completely dismantling these networks.

Dark Web Marketplace Disruptions
The dark web marketplace landscape continued to evolve in 2024-2025, with law enforcement achieving several notable takedowns:
- Nemesis Market: German authorities dismantled the infrastructure of this darknet cybercrime marketplace in March 2024, seizing approximately $100,000 in cash. Nemesis Market had served as a hub for illegal drugs, stolen data, and cybercrime services.
- LabHost Takedown: In April 2024, the UK's Metropolitan Police Service disrupted LabHost (also known as LabRat), a Phishing-as-a-Service (PhaaS) provider that offered phishing pages targeting banks and prominent organizations globally.
- MATRIX Platform Dismantled: Operation Passionflower successfully took down MATRIX, an encrypted messaging platform used by cybercriminals to coordinate illegal activities while evading law enforcement. The operation involved multiple European countries and was coordinated by Europol and Eurojust.
Despite these successful takedowns, new marketplaces continued to emerge throughout 2024-2025, including Abacus Market and STYX Market, which quickly rose to prominence as AlphaBay's successor.
The Rise of International Cooperation
A notable trend throughout 2024-2025 has been the increasing effectiveness of international cooperation among law enforcement agencies. Major operations have involved unprecedented levels of coordination across borders, with agencies from dozens of countries working together under the coordination of organizations like INTERPOL, Europol, and the FBI.
This cooperation has been essential in combating cybercriminals who operate across multiple jurisdictions, using technological means to obscure their locations and identities.
However, challenges remain. As the U.S. Government Accountability Office (GAO) noted in a recent report, differences in how various agencies define and track cybercrime can hinder comprehensive understanding of the threat landscape. Efforts are underway to develop standardized categories of cybercrime to improve data collection and analysis.

Looking Ahead: New Frontiers in Cybercrime
As law enforcement tactics evolve, so do criminal strategies. Several emerging trends observed in 2024-2025 point to the future direction of cybercrime:
- Decentralization: Following major takedowns, criminal networks are increasingly adopting decentralized structures that lack clear leadership hierarchies, making them more resilient to law enforcement actions.
- AI-Enhanced Attacks: Artificial intelligence tools are being leveraged by cybercriminals to create more convincing phishing campaigns and to automate attacks, reducing the technical expertise needed to conduct sophisticated operations.
- Cross-Platform Operations: Criminals are expanding beyond traditional dark web forums to utilize mainstream platforms like Telegram for coordination and commerce, blurring the lines between the dark web and more accessible communication tools.
- Harsher Ransomware Payment Regulations: As governments begin to implement stricter rules around ransomware payments, the cybercrime landscape will likely adapt to these new restrictions.

Conclusion
The period of 2024-2025 has demonstrated both the growing sophistication of global cybercrime and the increasing effectiveness of coordinated law enforcement responses. While significant victories have been achieved in dismantling major criminal networks and infrastructure, the adaptability of cybercriminals ensures that this remains an ongoing battle.
The successes of operations like Cronos, Red Card, and Moonlander highlight the critical importance of international cooperation, intelligence sharing between public and private sectors, and continuous innovation in investigative techniques. As digital crime continues to evolve, so too must the global response to combat it effectively.

This article was compiled based on information from law enforcement press releases, cybersecurity research reports, and news coverage of major cybercrime operations conducted between 2024 and 2025.



















