Global Cybercrime Takedowns in 2025: A Year of Unprecedented Law Enforcement Action

Sustaining Momentum from 2024's Banner Year
The cybersecurity landscape in 2025 has been marked by an extraordinary acceleration of international law enforcement cooperation, building on the remarkable successes of 2024. Law enforcement actions in 2024 had already disrupted the activity of some of the most prolific cybercriminal groups, from those involved in botnets and phishing to distributed-denial-of-service (DDoS) attacks and ransomware, with LockBit being the most significant ransomware-as-a-service group severely impacted under Operation Cronos.
As we move through 2025, this momentum has not only continued but intensified, with authorities executing some of the most comprehensive and coordinated cybercrime takedowns in history. From dismantling major ransomware operations to seizing critical cybercrime infrastructure, the first half of 2025 has demonstrated that law enforcement agencies worldwide are operating with unprecedented coordination and effectiveness.
Bottom Line Up Front: 2025 has already witnessed more than a dozen major international cybercrime takedowns, resulting in hundreds of arrests, the seizure of thousands of servers, and the disruption of criminal networks affecting millions of victims globally.

Operation Talent: Dismantling the World's Largest Cybercrime Forums
January 2025: Cracked and Nulled Marketplace Takedown
In late January 2025, international law enforcement executed "Operation Talent," a coordinated takedown of two of the world's largest cybercrime forums: Cracked and Nulled. These platforms had over 10 million users combined and hosted more than 71 million posts related to cybercrime tools and stolen information.
Scale of the Operation:
- 17 servers seized across multiple countries
- Two suspects arrested in Valencia, Spain
- Over 50 electronic devices confiscated
- €300,000 in cash and cryptocurrency seized
- 12 domains within the Cracked and Nulled platforms taken down
Criminal Enterprise Details: The Cracked marketplace had been operating since March 2018, selling stolen login credentials, hacking tools, and hosting services. It claimed over four million users, hosted 28 million ads for cybercrime tools, and generated roughly $4 million in revenue. Nulled had been active since 2016, with over 5 million users and more than 43 million posts advertising cybercrime tools and stolen information, generating approximately $1 million in yearly revenue.
International Cooperation: The operation involved law enforcement authorities from the United States, Italy, Spain, Germany, France, Greece, Australia, and Romania, demonstrating the global reach required to combat modern cybercrime networks.
Associated Services Disrupted: The takedown extended beyond the forums themselves:
- Sellix, a financial processor used by Cracked for payments
- StarkRDP, a hosting service promoted on both platforms and run by the same suspects

Operation Phobos Aetor: 8Base Ransomware Gang Neutralized
February 2025: Major Ransomware Infrastructure Dismantled
In February 2025, a coordinated international law enforcement operation took down the dark web data leak and negotiation sites associated with the 8Base ransomware gang, with four Russian nationals arrested in Thailand.
Operational Impact:
- 27 servers seized and taken offline
- Four Russian nationals arrested as part of Operation Phobos Aetor
- Over 400 companies worldwide warned about ongoing or imminent 8Base ransomware attacks
- More than 40 pieces of evidence seized, including mobile phones, laptops, and digital wallets
Criminal Network Structure: 8Base operated as part of the broader Phobos ransomware ecosystem, using a Ransomware-as-a-Service (RaaS) model that made it accessible to a range of criminal actors, from individual affiliates to structured criminal groups. The U.S. Justice Department charged Roman Berezhnoy, 33, and Egor Nikolaevich Glebov, 39, both Russian citizens, as operators of the "8Base" and "Affiliate 2803" platforms.
International Coordination: Law enforcement agencies in Belgium, the Czech Republic, France, Germany, Japan, Poland, Romania, Singapore, Spain, Sweden, Switzerland, Thailand, the UK, and the US participated in the takedown.
High-Profile Targets: 8Base had claimed responsibility for high-profile attacks on the United Nations Development Programme and the Atlantic States Marine Fisheries Commission.
Bulletproof Hosting Infrastructure Destroyed
February 2025: Zservers/XHost Takedown
Dutch police physically seized 127 servers from the Zservers/XHost bulletproof hosting service at a data center in Amsterdam, following international sanctions announced by the U.S., U.K., and Australia.
Criminal Infrastructure Details: Zservers/XHost, operated by Russian nationals Alexander Igorevich Mishin and Aleksandr Sergeyevich Bolshakov, was accused of facilitating LockBit ransomware attacks and supporting cybercriminals' efforts to launder illegally obtained money. The hosting provider knowingly backed these malicious activities and even advertised its lax policies to potential customers.
Services Provided to Criminals:
- Anonymous hosting with promised protection from law enforcement
- Cryptocurrency payment processing for anonymity
- Infrastructure used by major cybercrime groups such as Conti and LockBit
- Hosting for websites, hacking tools and data stolen from victims
Unique Intelligence Operations: In a remarkable display of offensive cyber capabilities, the Australian Signals Directorate (ASD) had previously infiltrated Zservers' infrastructure to delete 520 GB of stolen healthcare data. ASD reported deleting as much as 250 TB of data from adversary systems stolen from Australia, the U.S., U.K. and other victims worldwide.

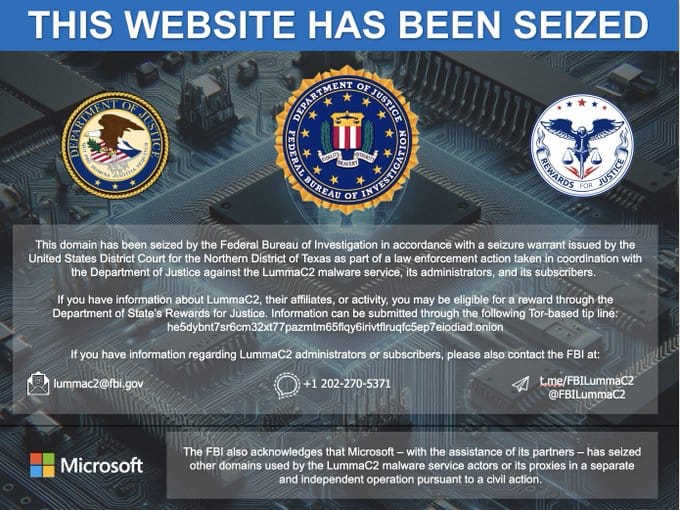
LummaC2 Information-Stealer Malware Disrupted
May 2025: Coordinated Domain Seizures
Building on the momentum from earlier operations, the Justice Department's takedown of LummaC2 malware infrastructure in May 2025 demonstrated continued effectiveness in targeting information-stealing operations. The seizure of five critical domains, combined with Microsoft's parallel civil action targeting 2,300 additional domains, showcased the evolving public-private partnership model that has become a hallmark of modern cybercrime enforcement.
Legislative and Policy Developments
UK Government Proposes Ransom Payment Ban
On January 14, 2025, the UK government unveiled a proposed framework implementing a payment prevention and reporting regime that would require companies to report all ransomware incidents and declare whether they intend to pay a ransom. The government proposed banning public bodies and infrastructure providers from making ransom payments to cyber attackers.
Three-Pillar Approach:
- Targeted Payment Ban: A ban on ransomware payments by public sector bodies, local authorities, and owners/operators of critical national infrastructure, extending current government policy that prohibits central government departments from making such payments.
- Payment Prevention Regime: Organizations not covered by the ban would be required to report their intention to pay a ransom to authorities before proceeding with payment.
- Mandatory Incident Reporting: Businesses and individuals affected by ransomware would be required to report attacks to authorities regardless of payment intention.
Global Significance: Jamie MacColl, a research fellow at the Royal United Services Institute, called the proposals "the most significant intervention against ransomware by any national government to date".

Emerging Trends and Patterns
Fragmentation of the Ransomware Landscape
Law enforcement takedowns have resulted in a 30% increase in the number of active ransomware groups, while the number of victims named on leak sites has remained relatively stable. This fragmentation means that a larger number of groups are listing roughly the same number of victims, pointing to entropy in the ransomware landscape.
Evolution of Criminal Adaptation
The speed with which criminal groups attempt to rebuild operations after takedowns has become a key focus for law enforcement. When LummaC2 administrators quickly established three replacement domains after the initial seizure, law enforcement was ready and seized these new domains within 24 hours, demonstrating the improved intelligence and operational capabilities of modern cybercrime units.
International Cooperation at Scale
The complexity and scope of 2025's operations reflect unprecedented levels of international cooperation:
- Operation Talent involved eight countries across three continents
- Operation Phobos Aetor coordinated agencies from 14 different nations
- Zservers takedown combined sanctions from three major allies with physical seizures in the Netherlands

Impact on Criminal Ecosystems
Financial Disruption
Following law enforcement takedowns of major gangs like LockBit and AlphV/BlackCat in 2024, extortion payments dropped 35% compared to 2023 — from $1.25 billion to $812.55 million. The continued pressure in 2025 suggests this downward trend is likely to continue.

Operational Challenges for Criminals
Each successful takedown creates cascading effects throughout the cybercriminal ecosystem:
- Trust Erosion: Law enforcement activity has achieved one of its intended objectives: undermine the trust of ransomware affiliates in the most prolific proponents of the RaaS model by damaging their reputations
- Infrastructure Costs: Criminals must invest more resources in redundant systems and security measures
- Recruitment Difficulties: High-profile arrests make criminal organizations less attractive to potential recruits
Defensive Intelligence Gains
The seizure of Cracked and Nulled forums provided law enforcement with "e-mail addresses, IP addresses and communication channels of the approximately 10 million registered user accounts" as the basis for further investigations.

Technology and Tactics Evolution
Enhanced Infiltration Capabilities
The investigation into Phobos that began in 2019 allowed investigators to infiltrate operations and gain intelligence that helped protect hundreds of targets. This demonstrates the long-term intelligence development required for successful modern cybercrime operations.
Coordinated Timing
Modern takedowns involve precise timing across multiple jurisdictions:
- Operation Talent took place over just two days in late January, involving coordinated raids on seven properties across multiple countries
- Real-time coordination prevents criminals from warning associates or destroying evidence
Public-Private Integration
The evolution of public-private partnerships has become crucial:
- Microsoft's independent action against 2,300 LummaC2 domains complemented government seizures
- Private sector partners such as Bitdefender, Cryptolaemus and Shadowserver contributed to Operation Endgame

Regional and Sector-Specific Impacts
Healthcare Under Siege
Since 2021, the Medusa ransomware group has been actively targeting sectors such as medical, education, legal, insurance, technology, and manufacturing, employing phishing campaigns to steal credentials and operating on a double extortion model.
Critical Infrastructure Focus
The FBI warned that Phobos had been used in attacks targeting local governments, emergency services, public healthcare, and other critical infrastructure entities across the United States.
Financial Sector Vulnerabilities
From January to September 2023 alone, credit card fraud caused losses of around ¥40.2 billion (~$287 million USD) in Japan, mostly due to phishing and stolen card data misuse.

Looking Forward: Challenges and Opportunities
Persistent Challenges
Despite remarkable successes, significant challenges remain:
- Geographic Safe Havens: Many cybercriminals operate from jurisdictions with limited international cooperation
- Technical Evolution: Criminal techniques continue to evolve, requiring constant adaptation by law enforcement
- Scale of the Problem: Global cybercrime costs are projected to reach $10.5 trillion annually by 2025, growing by 15% each year

Emerging Opportunities
2025's successes point to several promising developments:
- Enhanced Intelligence Sharing: Improved real-time coordination between international partners
- Private Sector Integration: More sophisticated public-private partnerships
- Proactive Disruption: Moving from reactive investigation to proactive disruption of criminal operations
Sustainability Questions
As one analysis noted, "2024 was a banner year for law enforcement agency actions against ransomware and cybercrime groups. Will the new administration ensure this momentum continues?" The answer appears to be a resounding yes, based on the scale and sophistication of 2025's operations.

Conclusion: A New Era of Cybercrime Enforcement
The cybercrime takedowns of 2025 represent more than isolated victories—they signal a fundamental shift in how the international community approaches digital crime. The level of coordination, technical sophistication, and sustained pressure demonstrated in operations like Talent, Phobos Aetor, and the various infrastructure seizures shows that law enforcement has adapted to meet the challenge of modern cybercrime.
As Allan Liska from Recorded Future noted, "We saw a strong law enforcement presence targeting ransomware groups in 2024 and it is great to see this continue into 2025. Sustained law enforcement action appears to be one of the best ways to slow down ransomware attacks".
The integration of legislative initiatives like the UK's proposed ransom payment ban with operational takedowns creates a comprehensive approach that addresses both the supply and demand sides of the cybercrime economy. While criminals will undoubtedly continue to adapt and evolve, the events of 2025 demonstrate that the days of operating with impunity are increasingly over.
The message from law enforcement is clear: no criminal network is too sophisticated, no infrastructure too distributed, and no operation too well-hidden to escape justice when the international community works together with sustained focus and adequate resources.
As we move through the remainder of 2025, the foundation laid by these early successes suggests that this may indeed be remembered as the year when the tide definitively turned in the fight against global cybercrime.

The operations detailed in this analysis involved agencies from more than 20 countries and resulted in the seizure of over 2,000 servers, hundreds of arrests, and the disruption of criminal networks affecting millions of victims worldwide.